

Why validate your cyber defenses?
Standardized declarative audit processes meet regulatory requirements but are not sufficient to demonstrate real-world capabilities in complex attack scenarios.
Whether it involves your human defense capabilities, technological defenses, or crisis management abilities, Erium offers solutions tailored to each of your needs.

Erium has developed a unique expertise in the European market
Supporting organizations in deploying advanced continuous validation methods for their ability to stop cyberattacks.
These approaches are based on the continuous execution of attack simulations through a Breach and Attack Simulation platform and CERT expertise.
The right technologies address your key questions:
Address strategic cybersecurity challenges
At the 2023 Assises, François Enaud, a board member of several international companies, engaged in a discussion with Arnaud Le Men, CEO of Erium, about the growing demand from executives for proof of cybersecurity effectiveness. Together, they explained how Breach and Attack Simulation is a game-changer, enabling organizations to address various strategic cybersecurity challenges.

Enhance Red-Team and Purple-Team operations
Human audits (Red-Team, Purple-Team, Pentest) are essential for improvement. However, they are costly and complex. With an automated approach, you can significantly boost their effectiveness.
Erium’s teams of auditors and offensive security experts, trained and certified in the use of the BlackNoise platform, are equipped to stress-test your entire defensive systems across any IT, industrial, or cloud environment.

Conduct a comprehensive assessment
With the evaluation of your cyber defenses, you will be able to assess:
– The effectiveness of your internal or external detection services (SOC) and incident response teams (CERT)
– The configuration of your detection technologies (EDR, NDR, CTI, ID/PS, FW, PXY, etc.)
– The sustained performance of your defense systems over time
– The evolution and control of your attack surface
How does Breach and Attack Simulation work?
Attack
Breach and Attack Simulation enables the configuration and automation of attack scenarios in real-world conditions, replicating simple or complex attacks across any IT, industrial, or cloud environment.
Measure
Each attack simulation assesses the effectiveness of your teams’ detection and response capabilities. This cyber score, based on the MITRE ATT&CK framework, allows you to measure the effectiveness of your investments, teams, and subcontractors, as well as demonstrate compliance with regulatory commitments.
Strengthen
Breach and Attack Simulation allows you to immediately assess your level of cyber defense effectiveness, enabling you to correct vulnerabilities and improve your system after facing real-world attack conditions.
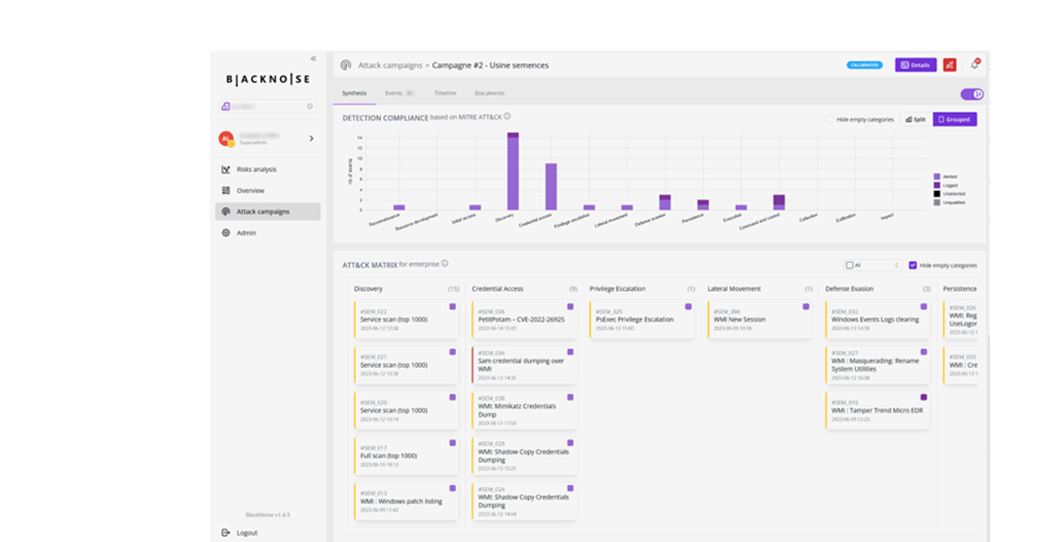
Focus on BlackNoise features
SecOps solutions training
- Simulation catalog
- Immediate results, 0 false positives
- Enhancement of detection tools with Sigma, Yara, Suricata rules, etc.
- Regular monitoring of security configuration
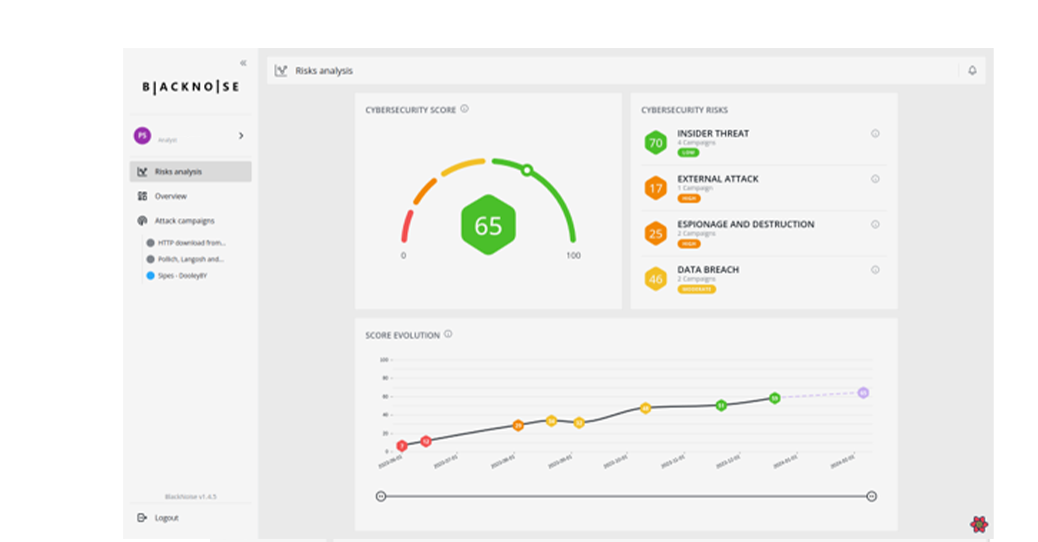
Focus on BlackNoise features
Overall cyber effectiveness score
- Defense level determined against major cyber risks
- Selection of appropriate scenarios
- Ongoing measurement of progress
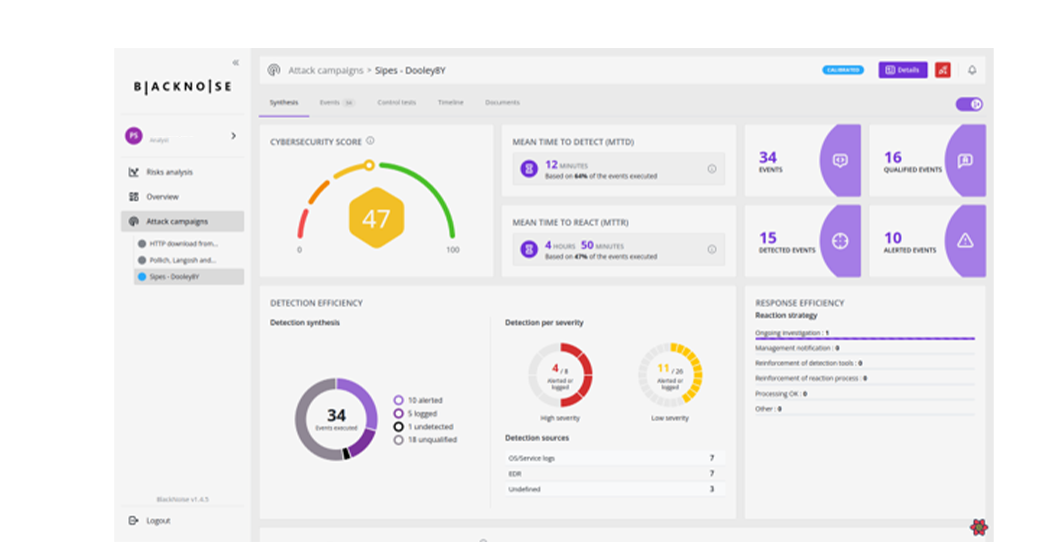
Focus on BlackNoise features
Vulnerability management
- Measurement of operational cybersecurity
- Detection KPIs (MTTD) and response KPIs (MTTR)
- Identification of SPOFs (Single Points of Failure) and high-value targets
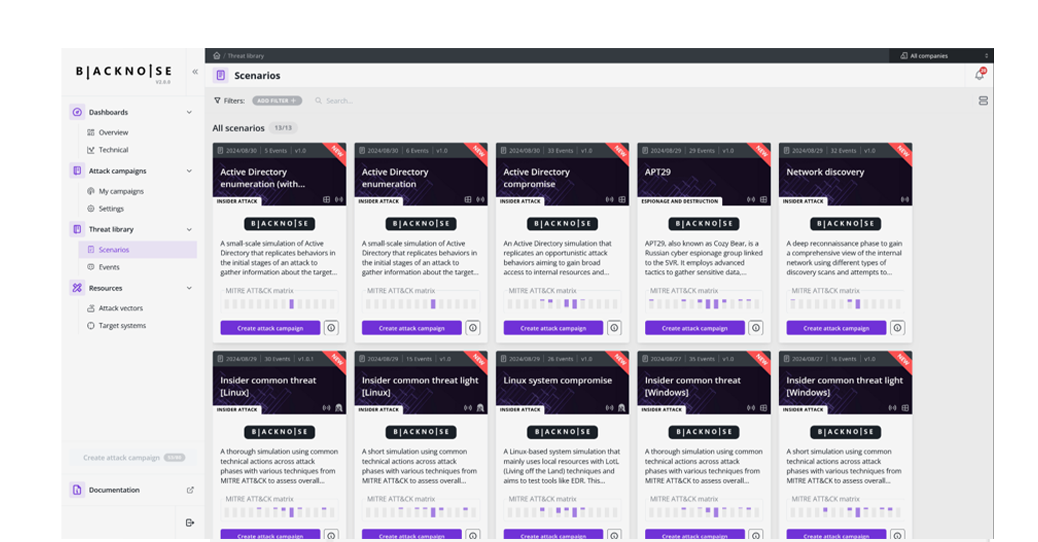
Focus on BlackNoise features
Scenarios built based on real-world attack methods
- Events and scenarios based on the MITRE ATT&CK framework
- Execution across all environments (Cloud / OT / IT)
- Customization of simulations to address emerging cyber threats
The technical evaluation of defense capabilities is essential to understand the resilience of IT, OT, and cloud environments.

Never trust, always check.
Challenging cyber defenses in real-world conditions allows you to prove their effectiveness and continuously enhance their performance. These approaches are standardized in certain countries, such as the United States. Would you like more information on this approach? Our experts are here to support you and implement the best processes and technologies.
Stay up-to-date with the latest in cybersecurity news
Latest technical indicators, press articles, white papers, cybersecurity monitoring, webinars, market trends, expert insights, solutions, glossary.







